Social Media
Facebook bug let websites read ‘likes’ and interests from a user’s profile

Facebook has fixed a bug that let any website pull information from a user’s profile — including their ‘likes’ and interests — without that user’s knowledge.
That’s the findings from Ron Masas, a security researcher at Imperva, who found that Facebook search results weren’t properly protected from cross-site request forgery (CSRF) attacks. In other words, a website could quietly siphon off certain bits of data from your logged-in Facebook profile in another tab.
Masas demonstrated how a website acting in bad faith could embed an IFRAME — used to nest a webpage within a webpage — to silently collect profile information.
“This allowed information to cross over domains — essentially meaning that if a user visits a particular website, an attacker can open Facebook and can collect information about the user and their friends,” said Masas.
The malicious website could open several Facebook search queries in a new tab, and run queries that could return “yes” or “no” responses — such as if a Facebook user likes a page, for example. Masas said that the search queries could return more complex results — such as returning all a user’s friends with a particular name, a user’s posts with certain keywords, and even more personal demographics — such as all of a person’s friends with a certain religion in a named city.
“The vulnerability exposed the user and their friends’ interests, even if their privacy settings were set so that interests were only visible to the user’s friends,” he said.
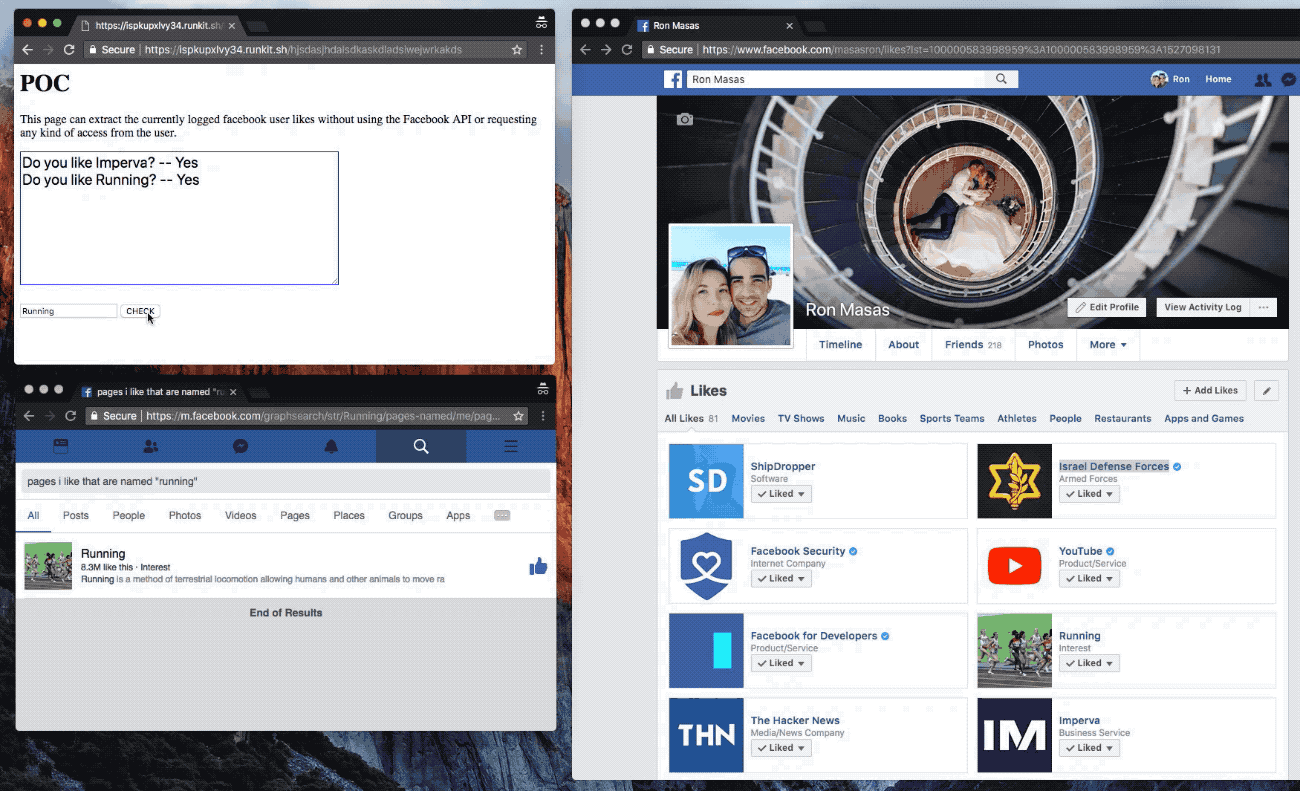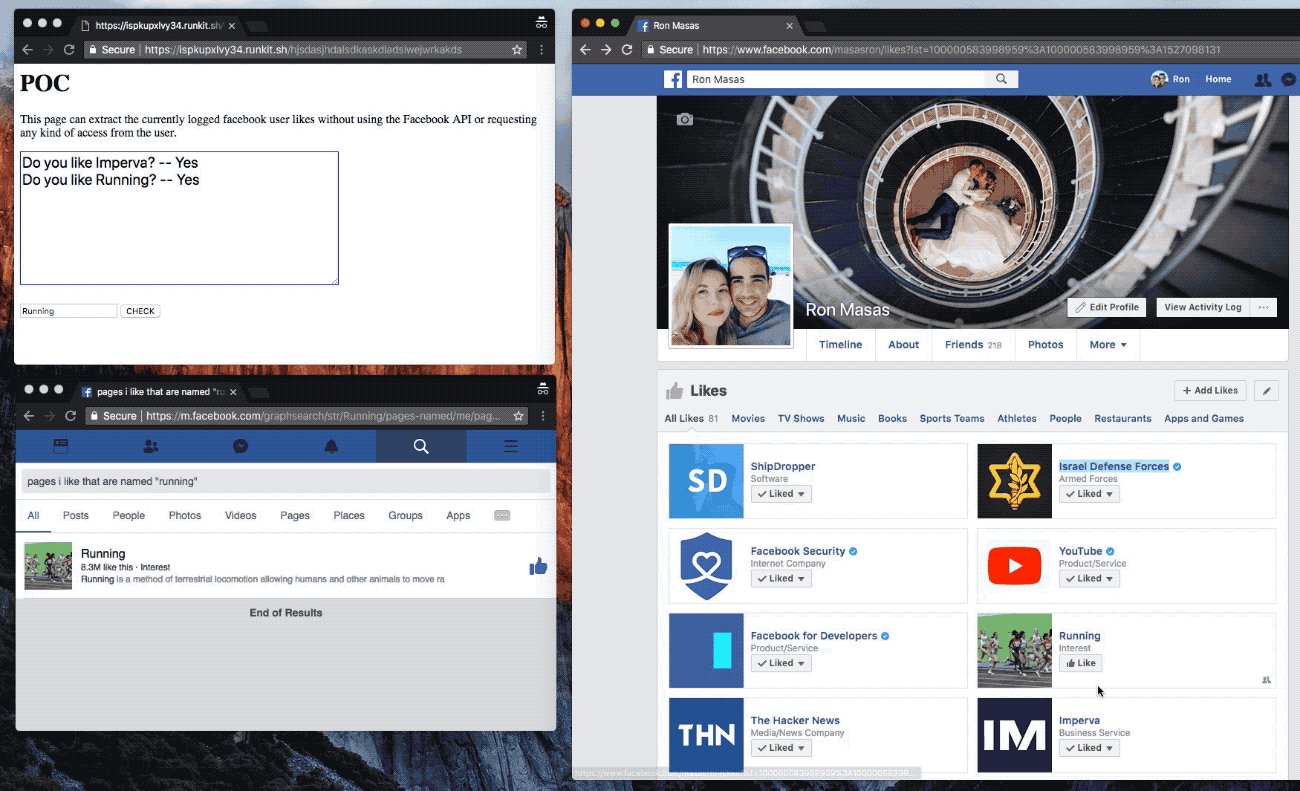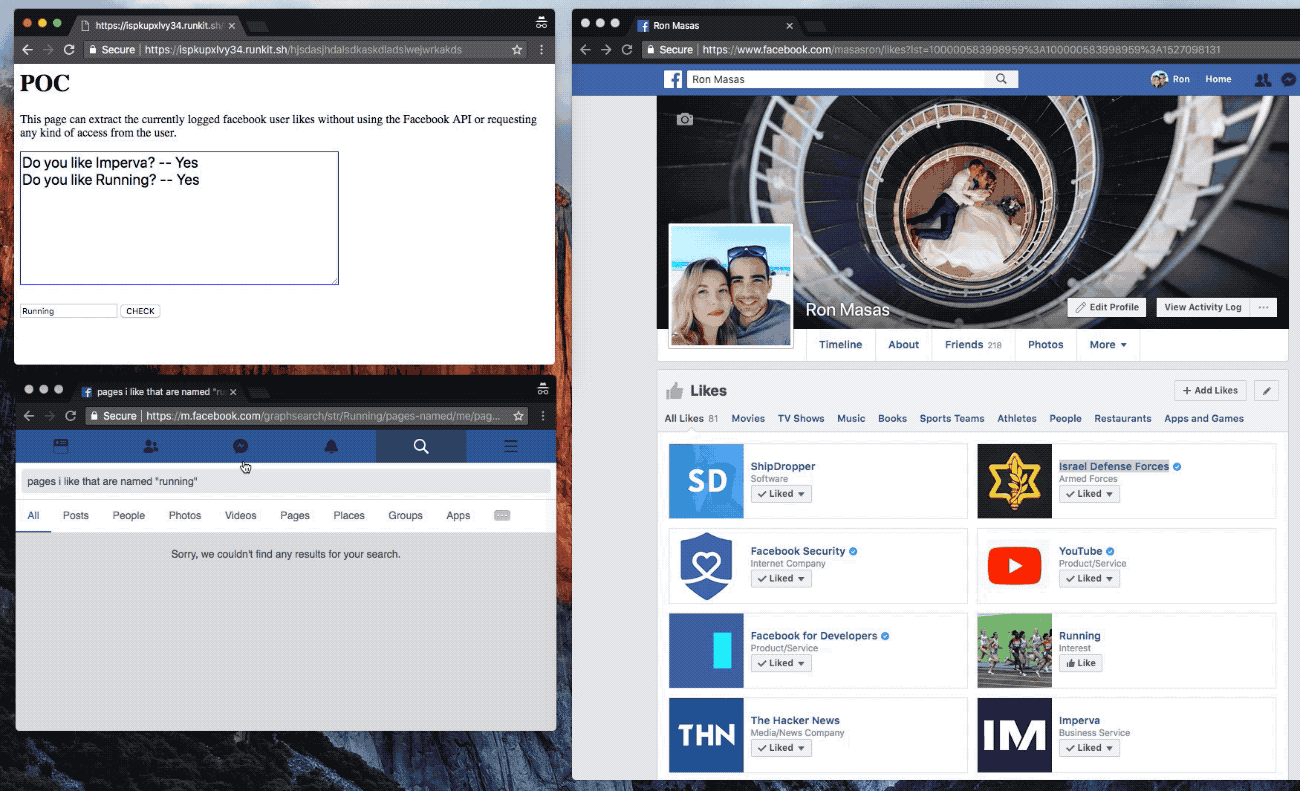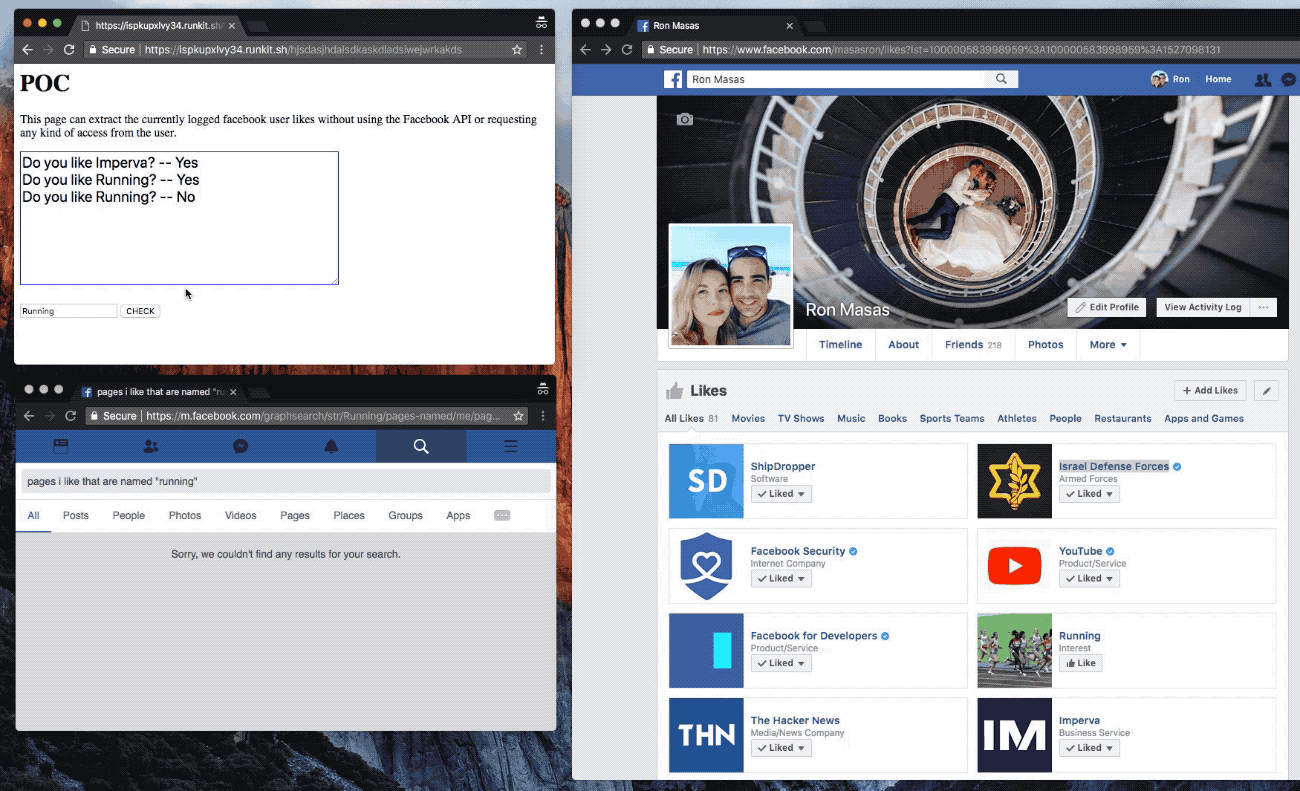
A snippet from a proof-of-concept built by Masas to show him exploiting the bug. (Image: Imperva/supplied)
In fairness, it’s not a problem unique to Facebook nor is it particularly covert. But given the kind of data available, Masas said this kind of data would be “attractive” to ad companies.
Imperva privately disclosed the bug in May. Facebook fixed the bug days later by adding CSRF protections and paid out $8,000 in two separate bug bounties.
Facebook told TechCrunch that the company hasn’t seen any abuse.
“We appreciate this researcher’s report to our bug bounty program,” said Facebook spokesperson Margarita Zolotova in a statement. “As the underlying behavior is not specific to Facebook, we’ve made recommendations to browser makers and relevant web standards groups to encourage them to take steps to prevent this type of issue from occurring in other web applications.”
It’s the latest in a string of data exposures and bugs that have put Facebook user data at risk after the Cambridge Analytica scandal this year, which saw a political data firm vacuum up profiles on 87 million users to use for election profiling — including users’ likes and interests.
Months later, the social media giant admitted millions of user account tokens had been stolen from hackers who exploited a chain of bugs.
-

 Business6 days ago
Business6 days agoAPI startup Noname Security nears $500M deal to sell itself to Akamai
-

 Business7 days ago
Business7 days agoUS think tank Heritage Foundation hit by cyberattack
-

 Entertainment6 days ago
Entertainment6 days agoNASA discovered bacteria that wouldn’t die. Now it’s boosting sunscreen.
-

 Entertainment6 days ago
Entertainment6 days agoHow to watch ‘Argylle’: When and where is it streaming?
-

 Business5 days ago
Business5 days agoTesla drops prices, Meta confirms Llama 3 release, and Apple allows emulators in the App Store
-

 Business4 days ago
Business4 days agoTechCrunch Mobility: Cruise robotaxis return and Ford’s BlueCruise comes under scrutiny
-

 Entertainment5 days ago
Entertainment5 days ago‘The Sympathizer’ review: Park Chan-wook’s Vietnam War spy thriller is TV magic
-

 Business3 days ago
Business3 days agoTesla layoffs hit high performers, some departments slashed, sources say




















