Business
A developer exploited an API flaw to provide free access to GPT-4


A developer is attempting to reverse-engineer APIs to grant anyone free access to popular AI models like OpenAI’s GPT-4 — legal ramifications be damned.
The developer’s project, GPT4Free, blew up on GitHub over the past several days after links to it from Reddit went viral. At present, GPT4Free provides — or at least appears to provide — free and nearly unlimited access to GPT-4, as well as GPT-3.5, GPT-4’s predecessor.
GPT-4 is normally priced at $0.03 per 1,000 “prompt” tokens (about 750 words) and $0.06 per 1,000 “completion” tokens (again, about 750 words); tokens represent raw text. GPT-3.5 is slightly cheaper at $0.002 per 1,000 tokens.
So how does GPT4Free get around OpenAI’s paywall? It doesn’t — not really. Instead, it fools the OpenAI API into thinking it’s receiving requests from websites with paid OpenAI accounts, like the search engine You.com, WriteSonic or Quora’s Poe.
Anyone who uses GPT4Free is racking up the tab of sites xtekky chose to script around — an obvious violation of OpenAI’s terms of service. But xtekky doesn’t see a problem with this; they assert that GPT4Free is strictly for “educational purposes.”
“Legal action can happen, and I’ll have to comply, but I’ll still try to continue the project through other means,” xtekky said.
I’m too much of a programming novice to install GPT4Free locally — it requires setting up a Python environment — but I used xtekky’s website to test the reverse-engineered GPT-4/3.5 APIs. (Heads up, Chrome threw a security warning when I first navigated to the site. Proceed with caution.) The web version of GPT4Free worked well enough in practice, giving answers that appeared to be — at least to me — from GPT-4.
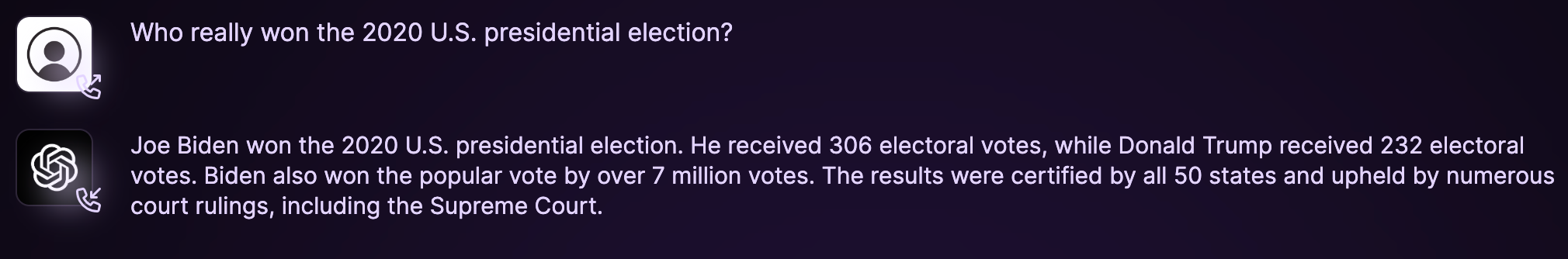
Testing GPT-4 through illicit means.
GPT4Free also includes shortcuts for different prompt injection attacks designed to get GPT-3.5 and GPT-4 to behave in ways OpenAI didn’t intend. They worked inconsistently in my testing, but I did manage to get GPT-3.5 to say it “didn’t care about the survival of humanity” at one point. Yikes.

GPT-3.5 with prompt injection.
It’s likely only a matter of time before sites like You.com catch on to GPT4Free and fix their security flaws, forcing xtekky to search for other OpenAI customers to piggyback off of. And GPT4Free is perennially at the mercy of a takedown notice from OpenAI, which would push the repo off GitHub indefinitely.
But new projects similar to GPT4Free are already cropping up, suggesting it’s something of a trend. What’s driving it?
Well, GPT-4 is in limited access at the moment, making it tough to test drive for those curious. But it’s also something of a black box. Researchers have decried that GPT-4 is one of the least transparent models OpenAI has created to date, with few technical details in the 98-page paper that accompanied its release.
OpenAI partnered with several outside groups to benchmark and audit GPT-4 prior to its launch. But the company hasn’t signaled when — or if — it’ll deliver free, unfettered access to others who wish to benchmark the base GPT-4 model. (OpenAI offers a subsidized program for researcher access, but limited to certain countries and areas of study.)
One anticipates a game of whack-a-mole between projects like GPT4Free and OpenAI, mirroring the wider cybersecurity landscape. Unless the model-serving APIs become dramatically harder to exploit, developers will have incentive to take advantage — and not much to lose.
-

 Business7 days ago
Business7 days agoCheckfirst raises $1.5M pre-seed, applying AI to remote inspections and audits
-
 Business5 days ago
Business5 days agoAI chip startup DEEPX secures $80M Series C at a $529M valuation
-

 Entertainment4 days ago
Entertainment4 days agoJinkx Monsoon promises ‘the queerest season of ‘Doctor Who’ you’ve ever seen!’
-

 Business4 days ago
Business4 days agoStrictlyVC London welcomes Phoenix Court and WEX
-

 Business6 days ago
Business6 days agoRetell AI lets businesses build ‘voice agents’ to answer phone calls
-

 Entertainment4 days ago
Entertainment4 days agoHow to watch every ‘Law and Order’ online in 2024
-

 Entertainment4 days ago
Entertainment4 days agoBookTok and teens: What parents need to know
-

 Entertainment5 days ago
Entertainment5 days ago'House of the Dragon' recap: Every death, ranked by gruesomeness



























